PCI Compliance
Cisco Meraki provides a comprehensive solution to ensure a PCI compliant wireless environment held to the strict standards of a Level 1 PCI audit (the most rigorous audit level). Cisco Meraki's rich security feature set addresses all of the PCI Data Security Standards, helping customers to build and maintain a secure network, protect cardholder data, maintain a vulnerability management program, implement strong access control measures, and monitor network security.
Unlike traditional wireless LANs, Cisco Meraki's intelligent security infrastructure eliminates the management complexities, manual testing, and ongoing maintenance challenges that lead to vulnerabilities. Cisco Meraki's intuitive and cost effective security features are ideal for network administrators, while powerful and fine-grained administration tools, account protections, audits, and change management appeal to CISOs.
Centrally managed from the cloud, Cisco Meraki makes it easy and cost effective to deploy, monitor, and verify PCI compliant WiFi across distributed networks of any size.
PCI-DSS requirements applicable to wireless LANs and their related Cisco Meraki features:
- Cisco Meraki Infrastructure – Isolated from the Cardholder Data Environment
- Requirement 1.2.3 – Segregate Wireless Network and the Cardholder Data Environment
- Requirement 2.1.1 – Change Vendor Defaults and Enable Strong Encryption
- Requirement 4.1.1 – Encrypt Authentication and Transmission with Industry Best Practices
- Requirement 6.1 – Use the Latest Security Patches
- Requirement 7.2 – Restrict Access Based on a User's Need to Know
- Requirement 8 – Implement User-Based Access Controls
- Requirement 10 – Track and Monitor All Access to Network Resources
- Requirement 11.2/11.3 – Perform Regular Audits and Penetration Testing
- Requirement 11.1/11.4 – Detect Unauthorized Access
Cisco Meraki Infrastructure – Isolated from the Cardholder Data Environment
Cisco Meraki's cloud hosted WLAN controller is out of band, meaning that wireless traffic (including cardholder data) does not flow through Cisco Meraki's cloud-hosted controller or any other Cisco Meraki infrastructure not behind your firewall. Learn more about Cisco Meraki's out of band architecture. Cisco Meraki's datacenters are SAS70 type II certified, feature robust physical and cyber security protection, and are regularly audited by third parties. Learn more about Cisco Meraki's datacenters.
Requirement 1.2.3 – Segregate Wireless Networks and the Cardholder Data Environment
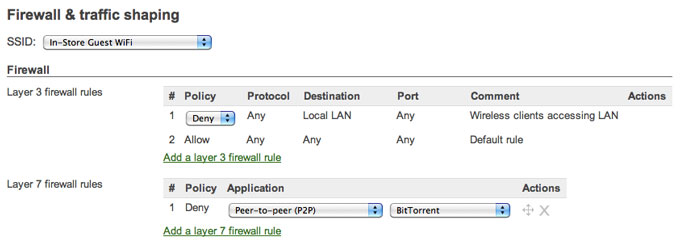
Cisco Meraki's wireless APs include an integrated stateful firewall which ensures that guest WiFi users and other non-privileged clients cannot access cardholder data, in conformance with Requirement 1.2.3. The firewall's LAN isolation feature enables one-click secure guest WiFi, wherein guests can only access the Internet. Blocked from LAN access, guests cannot spread viruses or reach internal resources. Cisco Meraki's firewall provides fine-grained control, from layer 3 through 7. Configure VLAN tags, ACLs, identity-based policies, and block unwanted applications - even peer-to-peer apps without well-known hosts and ports.
Requirement 2.1.1 – Change Vendor Defaults and Enable Strong Encryption
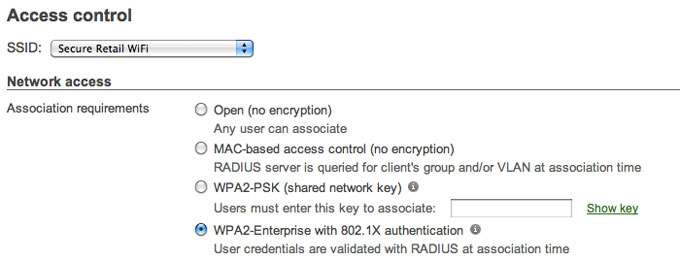
Cisco Meraki does not ship with default vendor keys that need to be changed. Cisco Meraki hardware is configurable through an SSL-encrypted connection, accessible only by authenticated users. To comlpy with Requirement 2.1.1, simply enable strong security standards, such as WPA2 (802.11i). See Requirement 4.1.1 for more information on wireless encryption.
Requirement 4.1.1 – Encrypt Authentication and Transmission with Industry Best Practices
Compliant networks require strong encryption using industry best-practices, e.g. WPA2, for wireless networks used for cardholder data. Cisco Meraki supports WPA2 (802.11i), offering both WPA2-PSK and WPA2-Enterprise with AES encryption. To maintain compliance with Requirements 4.1.1 and 2.1.1, enable WPA2 on any SSID that cardholder data is transferred over. Since Cisco Meraki's firewall will isolate traffic between SSIDs, WPA2 need not be enabled on SSIDs that are not used for cardholder data (e.g. a guest WiFi SSID.)
Requirement 6.1 – Use the Latest Security Patches
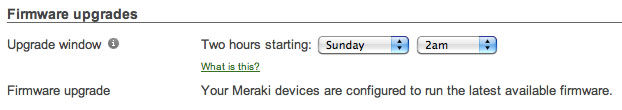
Cisco Meraki firmware updates are delivered seamlessly from the cloud to APs. When firmware updates are available, an administrator simply schedules an appropriate time for APs to download and install the new version, eliminating insecure and out of date firmware in the Cardholder Data Environment. This delivery model facilitates compliance with Requirement 6.1 – without deciphering compatibility matrices, time consuming manual updates, site visits to branch locations.
Requirement 7.2 – Restrict Access Based on a User's Need to Know
Cisco Meraki provides role-based administration to enforce the principle of least privilege in compliance with Requirement 7.2. Role-based administration lets you appoint administrators for specific subsets of your organization and specify whether they have read-only access to reports and troubleshooting tools, can administer managed guest access via Cisco Meraki's Lobby Ambassador, or can make configuration changes to the network.
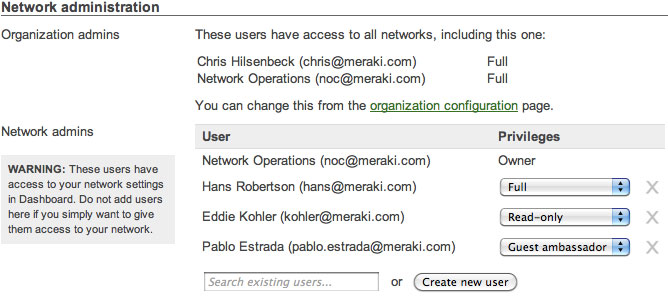
Requirement 8 – Implement User-Based Access Controls
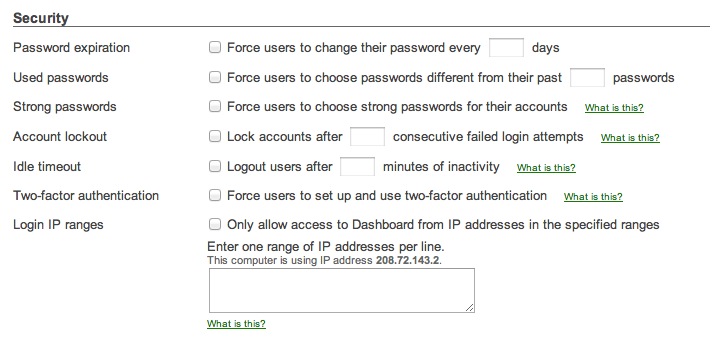
Cisco Meraki includes a comprehensive suite of features to enable unique ID and authentication methods for network administration, in compliance with Requirement 8. Configure organization-wide security policies for your Cisco Meraki administrator accounts to better protect access to the Cisco Meraki dashboard and network infrastructure. These policies include account protections such as two-factor authentication, password hardening policies, and the use of encrypted transmission (SSL/TLS) for access to the Cisco Meraki dashboard.
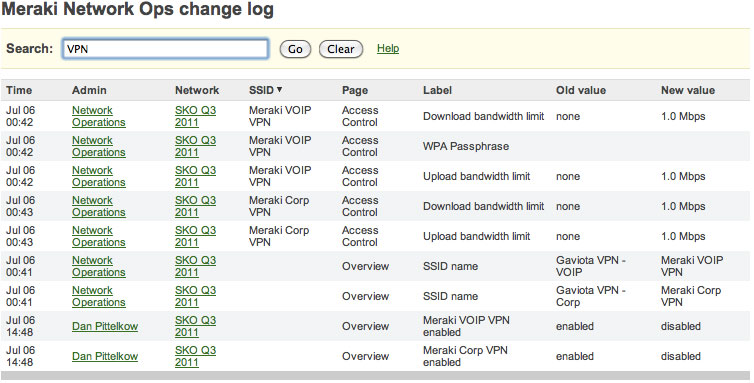
Requirement 10 – Track and Monitor All Access to Network Resources
Cisco Meraki logs the time, IP, and approximate location (city, state) of logged in administrators. Additionally, Cisco Meraki provides a searchable configuration change log, which indicates what configuration changes were made, who they were made by, and which part of the organization the change occurred in. Auditing this configuration and access information satisfies Requirement 10 and provides greater visibility into your network.
Requirement 11.2/11.3 – Perform Regular Audits and Penetration Testing
Cisco Meraki datacenters undergo thorough quarterly scans and daily penetration testing by McAfee SECURE, an Approved Scanning Vendor (ASV). Cisco Meraki is verified to be free of vulnerabilities such as injection flaws, cross-site scripting, misconfiguration, and insecure session management. Cisco Meraki datacenters are SAS70 type II certified, hardened against physical and network intrustion. These procedures exceed the scanning and penetration testing requirements of requirement 11.2 and 11.3, respectively.
Requirement 11.1/11.4 – Detect Unauthorized Access
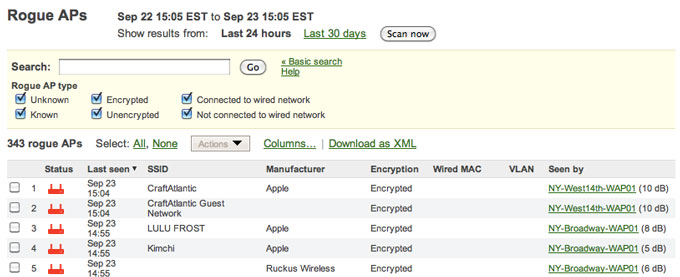
Cisco Meraki's out-of-the-box rogue AP detection protects the network from unauthorized wireless access points that may compromise network security. Rogue APs are unauthorized wireless APs that connect to your wired LAN, or that connect to a separate network but masquerade as part of your WLAN, using your same SSID. Cisco Meraki automatically detects rogue APs, identifying their IP address, VLAN, manufacturer, and model. Rogue detection includes network-wide visualization, email alerts, and reporting, meeting Requirements 11.1 and 11.4.