
Cisco Meraki WAN & Security
Featured Technologies
Next-Gen Firewall:
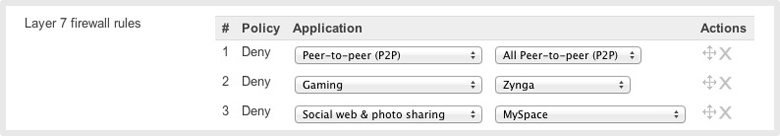
With the proliferation of modern applications and mixed-use networks, host and port based security is no longer sufficient. Cisco Meraki's layer 7 "next generation" firewall, included in MX security appliances and every wireless AP, gives administrators complete control over the users, content, and applications on their network.
Layer 7 traffic classification and control
The Cisco Meraki proprietary packet processing engine analyzes network traffic up to and including layer 7, using sophisticated fingerprinting to identify users, content, and applications on the network. Each network flow is categorized, and access control policies are enforced — for example, blocking Netflix and prioritizing video conferencing. By classifying traffic at layer 7, Cisco Meraki's next generation firewall controls evasive, encrypted, and peer-to-peer applications, like BitTorrent or Skype, that cannot be controlled by traditional firewalls. Cisco Meraki's next generation firewall is included in all wireless access points and security appliances.
Intrusion detection engine
Featuring an integrated intrusion detection and prevention (IDS / IPS) engine based on Sourcefire's Snort, the single most widely deployed intrusion detection and prevention technology in the world, Cisco Meraki security appliances protect your network against malicious entities and threats. Using a combination of signature, protocol and anomaly-based inspection methods ensures ironclad security for your network. Leveraging the Cisco Meraki cloud management platform, threat signatures are automatically updated, keeping security always up-to-date.
Identity-based and device-aware security
Device-aware access controls enable administrators to ensure the appropriate level of network access for each class of devices. Layer 7 device fingerprints automatically detect and classify Apple iOS, Android, Windows, Mac OS, and other clients. These fingerprints are integrated into Cisco Meraki firewalls and wireless APs, so that administrators can, for example, apply firewall rules specific to iPads in a Bring Your Own Device (BYOD) network.
Cisco Meraki security appliances feature a powerful category-based content filter, which matches content against millions of URLs in dozens of categories. The Cisco Meraki content filtering engine features native Active Directory integration to apply access controls specific to each class of users. Content lists and application signatures are updated dynamically from the cloud, so that security policies remain up to date even as content and applications change.
Intrusion Prevention:
Every network is a potential target for malicious attack; Cisco Meraki MX Security Appliances provide best-in-class, easily configurable intrusion prevention to protect yours.
Best-in-class Sourcefire Engine
Every Cisco Meraki MX Security Appliance supports unparalleled threat prevention via the integrated Sourcefire engine. Intrusion prevention (IPS) is performed via rulesets: pre-defined security policies that determine the level of protection needed. Sourcefire refreshes rulesets daily to ensure protection against the latest vulnerabilities—including exploits, viruses, rootkits, and more—and these are pushed via the cloud to MX customers within an hour—no manual staging or patching needed.
Easy Error-free Deployment
Human error can bedevil the best attempts to lock down a network if the security tool used is complex. Enabling and deploying IPS on the MX, however, takes mere seconds and involves only two dashboard clicks: enabling IPS, and selecting a Sourcefire ruleset (threat protection level) to enforce. Since vulnerability definitions are automatically pushed to the MX from the cloud, IT admins can enjoy up-to-date, market leading IPS with minimal effort.
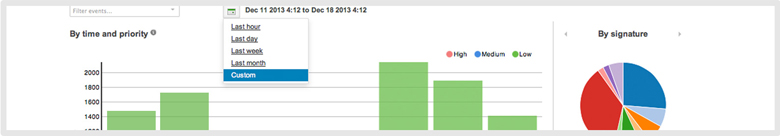
Real-time Graphical Reporting
View IPS security reports from any Internet-accessible device in the Meraki dashboard. Data is presented in real time, allowing IT admins to quickly gauge current threat status—as well as view historical trends—for informed decision-making. Use built-in templates to filter data from the last hour, day, week, or month—or create a custom date range view. Granular, by-the-minute details are also available. View specifics about detected threats and learn about about remediation techniques by following links to CVE, TechNet, and other resources intelligently presented within the Meraki dashboard. Finally, choose to view security threats organization-wide, or drill down for detailed reports on specific networks.
Use reports to identify troublesome clients and applications, make informed firewall or traffic-shaping decisions, provide a security synopsis to management, and gauge overall vulnerability over time.
Auto VPN:
Cisco Meraki’s unique auto provisioning site-to-site VPN connects branches securely, without tedious manual VPN configuration. Leveraging the power of the cloud, MX Security Appliances configure, monitor, and maintain your VPN so you don't have to.
Auto-provisioning IPsec VPN
Cisco Meraki’s unique auto provisioning site-to-site VPN connects branches securely with complete simplicity. Using IPsec over any wide area network, the MX links your branches to headquarters as well as to one another as if connected with a virtual Ethernet cable.
Automatically configured VPN parameters
MX Security Appliances automatically configure VPN parameters needed to establish and maintain VPN sessions. A unique cloud-enabled hole-punching and discovery mechanism enables automatic interconnection of VPN peers and routes across the WAN, and keeps them updated in dynamic IP environments. Security associations and phases, authentication, key exchanges, and security policies are all handled automatically by MX VPN peers. Site-to-site connectivity is established through a single click in the Cisco Meraki dashboard. Intuitive tools built in to the Cisco Meraki dashboard give administrators a real-time view of VPN site connectivity and health. Round trip time latency between peers and availability status information automatically keep track of all the VPN peers in the network.
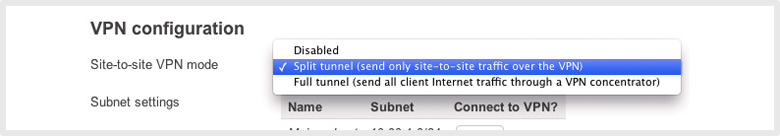
Flexible tunneling, topology, and security policies
Configurations for split-tunneling and full-tunneling back to a concentrator at headquarters are fully supported and configured in a single click. Hub-and-spoke and full mesh VPN topologies give deployment flexibility, and a built-in site-to-site firewall enables custom traffic and security policies that govern the entire VPN network.
Failover & HA:
Mission critical networks can’t afford downtime and disruption. Cisco Meraki MX Security Appliances support multiple layers of redundancy, ensuring WAN connectivity, appliance availability, and seamless failover for branch sites.
3G/4G Cellular & Dual Uplink Support
Every Cisco Meraki MX Security Appliance supports dual WAN uplinks with seamless, automatic failover—necessary for protection against ISP connection outage. In the event of failover, the MX's built-in traffic prioritization engine redirects flows and allocates capacity based on your prioritized application needs, ensuring smooth network operation. Supported uplinks include gigabit Ethernet and cellular comprised of 1xEV-DO, W-CDMA, and HSPA from major cellular carriers, as well as 4G cellular, including LTE and WiMAX.
Warm Spare Failover
Warm spare failover ensures the integrity of MX service at the appliance level regardless of deployment mode. In the event an MX goes offline, a secondary MX will automatically take over its duties—ensuring a site is not deprived of functionality like industry-leading intrusion prevention, VPN, application and client control, DHCP service, and more. The Meraki MX uses the Virtual Routing Redundancy Protocol (VRRP), so networked devices need no additional configuration or intervention to begin using the spare MX.
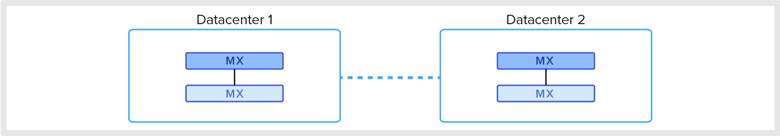
Datacenter High Availability (HA)
Datacenter failover is a mission critical requirement for organizations securely tunneling branch sites to datacenters. Cisco Meraki MX Security Appliances support secure tunneling between sites using either mesh or hub-and-spoke topologies. You can specify which datacenter to use as the primary resource for shared subnets, along with a list of other priority hubs to failover to in the event of outage. If a site goes offline, branches will automatically fail over to a secondary (or tertiary, etc.) datacenter that you specify.
WAN Optimization:
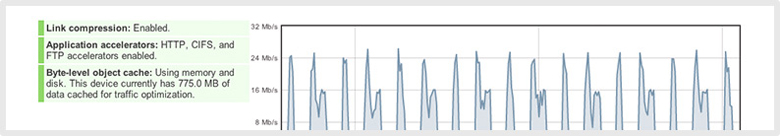
Cisco Meraki’s WAN optimization uses a combination of techniques to cut bandwidth consumption between branches and accelerate application performance by up to 209X. WAN optimization is included with every MX Security Appliance and is enabled with just two clicks.
Universal data store with de-duplication
A universal data store optimizes caching of data that needs to be transferred across the WAN by eliminating redundant data at the byte level and storing only the unique information needed represent data requested by users. A data redundancy elimination (DRE) algorithm identifies byte streams transferred in previous sessions and determines how much data needs to be transferred across the WAN. MXs include WAN optimization storage of up to 4 TB, enabling maximum WAN optimization for branches that have high inter-site bandwidth demands.
WAN link compression
Link compression accelerates WAN link performance, even for data that is not yet stored in the WAN optimization cache. Each peer-to-peer VPN link between branches is automatically compressed when WAN optimization is enabled.
Protocol-specific optimization
Beyond optimizing all TCP traffic, protocol-specific algorithms accelerate applications known to be particularly sensitive to high latency or slow bandwidth links. CIFS/SMB, FTP, and HTTP are optimized to reduce protocol inefficiencies, such as chattiness and round trip acknowledgement delays. WAN optimization can be limited to certain IP ranges and ports, and specific traffic can be excluded from optimization.
Content Filtering:
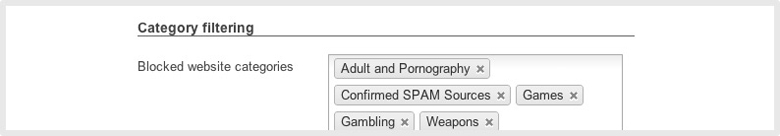
Cisco Meraki’s sophisticated content filtering enables the users of your network to enjoy the benefits of the Internet while remaining protected from inappropriate or harmful content, maintaining productivity and compliance with applicable business and regulatory requirements.
Identity-based filtering policies
Granular identity based policies can be tailored to specific groups wherever Active Directory is used, with whitelists providing a means to exclude certain users and websites from all filtering. Policy management of AD groups is handled directly in the dashboard, and direct queries of the AD server enable an intuitive interface without the need for AD-based setup or agents, reducing configuration steps and making group-based filtering a breeze.
Scalable database with SafeSearch integration
When a device attempts to access a web page, the address is checked against a database of URIs. Addresses are passed through a series of pattern matching steps so that, for example, access to a specific URL on a website may be allowed, with others excluded. Specific URL addresses can be added to a whitelist to take precedence over the filter. While filtering can traditionally be a complex and time-consuming activity, the Cisco Meraki solution provides improved workflows and greater efficiency for the network administrator.
Integration with Google and Bing SafeSearch enables a safe and secure internet environment with a single click. YouTube for Schools and YouTube EDU integration make managing educational content and access easy, and integrated web caching accellerates video and web downloads across the network.
Automatic, cloud-based signature updates
Cisco Meraki‘s content filtering is simple to administer, with more than 80 categories of websites available to be blocked to all but whitelisted users. Cisco Meraki’s MX Security Appliances work behind the scenes with the Cisco Meraki cloud, providing the network administrator with access to this powerful tool from a single pane-of-glass. Filtering signatures are updated automatically via the cloud, eliminating the need to manually purchase, track, or apply updates, and ensuring policies are always up to date.
