
Cisco Meraki MX400
Cloud-Managed Security Appliance for the Datacenter

מחירים נוספים מופיעים למטה, או לחצו כאן!
שימו לב: כל המחירים באתר כוללים מע"מ. החיוב יבוצע על פי שער "העברות והמחאות מכירה" של המטבע (דולר אמריקאי) ביום אישור ההזמנה.

Overview:
The Cisco Meraki MX400 is an integrated router, next-generation firewall, traffic shaper, and Internet gateway that is centrally managed over the web. The MX400 offers an extensive feature set, yet is incredibly easy to deploy and manage. Intuitive web-based administration eliminates specialized training and dedicated staff, and cloud-based centralized management provides seamless multi-site networks, automatic firmware upgrades, and much more.
MX400 Highlights
- SFP / SFP+ for 1G / 10G connectivity
- Swappable interface modules
- Stateful firewall throughput: 1 Gbps
- Redundant power supplies
- Supports approximately up to 2,000 users
Cloud-based centralized management
- Managed centrally over the Web
- Classifies applications, users and devices
- Zero-touch, self-provisioning deployments
Networking and security
- Stateful firewall
- Auto-provisioning site-to-site VPN
- Smart link bonding
- Active directory integration
- Layer 7 application visibility and traffic shaping
- Application prioritization
- Choose WAN uplink based on traffic type
WAN optimization
- Reduces intra-site bandwidth consumption
- Accelerates CIFS, FTP, HTTP, and TCP traffic
- WAN optimization cache: 1 TB
Advanced security services
- Client VPN (IPsec)
- Content filtering (CIPA compliant)
- Antivirus engine and antiphishing filtering
- Requires Advanced Security License
 A Complete Solution for Distributed Networks
A Complete Solution for Distributed Networks
The MX provides a complete networking and security solution that typically requires up to four appliances: branch router, next-generation firewall, Layer 7 traffic shaper, and CIPA-compliant content filter.
This integrated architecture dramatically reduces up-front costs and ongoing support and maintenance. Moreover, it provides unified, single pane-of-glass management, speeding deployment and eliminating the need for specialized training.
 The First Cloud Managed Networking and Security Platform
The First Cloud Managed Networking and Security Platform
The Cisco Meraki MX is a complete networking and security solution, designed to make distributed networks fast, secure, and easy to manage.
The MX is managed entirely through Cisco Meraki’s web based dashboard. Designed with intuitive controls for IT generalists, the MX requires no training or specialized staff. The MX will even self-provision, allowing for remote branch deployments without on site IT.
Powerful Hardware Platform
The MX hardware platform is purpose-built for cloud management, with CPU and memory resources designed to provide application and content-aware security at the edge. The MX's robust platform enables advanced features like layer 7 application traffic shaping, content filtering, antivirus/antiphishing, and site-to-site VPN, while providing the throughput and capacity for modern, high-density networks.
 Easy to Manage Without Training or On-Site Networking Expertise
Easy to Manage Without Training or On-Site Networking Expertise
The MX was designed for ease of use, even in branches without on-site IT. An intuitive interface, contextual help, and real-time support from the cloud eliminate specialized training. To deploy the MX in remote locations, simply connect the MX to the Internet, and it will securely self-provision from the cloud. Firmware upgrades, security patches, and signature updates are all delivered seamlessly from the cloud, ensuring that the MX is always up to date. Integrating broad security and networking features into a single intuitive device drastically reduces complexity in the branch.
 Secure, Reliable Distributed Networking Without Costly MPLS
Secure, Reliable Distributed Networking Without Costly MPLS
The MX eliminates costly MPLS tunnels with secure site-to-site VPN over redundant Internet connections. Using IPsec over the Internet, the MX links your branches to headquarters as well as to one another as if connected with a virtual Ethernet cable. Configuration headaches like NAT traversal are handled automatically from the cloud. The MX70's dual WAN ports with balancing and failover enable the use of redundant commodity Internet connections, providing more bandwidth and higher reliability than MPLS, at a fraction of the cost.
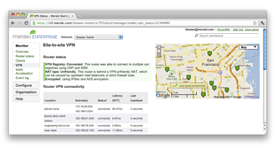 Connects and Secures Branches from the Cloud
Connects and Secures Branches from the Cloud
Cisco Meraki’s cloud management platform makes it easy to deploy secure, interconnected, centrally managed multi-site networks. Add new sites in seconds with auto-configuring VPN. Centrally manage user, content and application-aware firewall policies across your entire network.
Control Applications, Users, and Devices
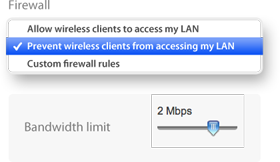
![]() The MX provides complete control over users, content, and applications, giving the visibility, security, and control required for mixed-use networks. Layer 7 fingerprinting technology lets administrators block objectionable content and applications and prevent recreational apps like BitTorrent from wasting precious bandwidth. Likewise, the MX can prioritize critical applications like voice and video. User fingerprinting identifies clients by name, operating system, or device (e.g. iPad). Fast search, automatic reports, and device quarantine provide complete visibility and control over the users across the entire network.
The MX provides complete control over users, content, and applications, giving the visibility, security, and control required for mixed-use networks. Layer 7 fingerprinting technology lets administrators block objectionable content and applications and prevent recreational apps like BitTorrent from wasting precious bandwidth. Likewise, the MX can prioritize critical applications like voice and video. User fingerprinting identifies clients by name, operating system, or device (e.g. iPad). Fast search, automatic reports, and device quarantine provide complete visibility and control over the users across the entire network.
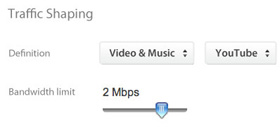 Increases WAN Performance and Reduces Bandwidth Costs
Increases WAN Performance and Reduces Bandwidth Costs
Block unwanted bandwidth hogs like BitTorrent, and add capacity with WAN load balancing. Cache, deduplicate, and optimize traffic with WAN optimization to lower bandwidth consumption by up to 99% and improve application performance by up to 209x.
Features:
 Multi-Site Cloud Management
Multi-Site Cloud Management
![]() The Cisco Meraki Cloud Networking architecture enables plug and play branch deployments and provides centralized visibility and control across any number of distributed locations.
The Cisco Meraki Cloud Networking architecture enables plug and play branch deployments and provides centralized visibility and control across any number of distributed locations.
MX security appliances self-provision – automatically pulling policies and configuration from the cloud – enabling branch deployments without on-site IT. The Cisco Meraki cloud delivers seamless firmware and security signature updates, automatically establishes site-to-site VPN tunnels, and provides automatic network monitoring and alerts.
Since the MX is managed entirely through the Cisco Meraki web-based dashboard, configuration and diagnostics can be performed remotely just as easily as they can be performed on-site, eliminating costly field visits. Even firmware updates are performed seamlessly, over the web.
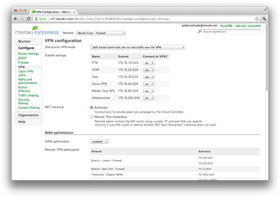 Auto VPN
Auto VPN
![]() Cisco Meraki's unique auto provisioning site-to-site VPN connects branches securely with complete simplicity. Using IPsec over any wide area network, the MX links your branches to headquarters as well as to one another as if connected with a virtual Ethernet cable.
Cisco Meraki's unique auto provisioning site-to-site VPN connects branches securely with complete simplicity. Using IPsec over any wide area network, the MX links your branches to headquarters as well as to one another as if connected with a virtual Ethernet cable.
Site-to-site connectivity is established through a single click in Cisco Meraki's dashboard. Gone are the configuration headaches of traditional site-to-site VPNs: route discovery, key negotiation, authentication, security policies, crypto maps, and access lists are all handled automatically from the cloud.
Ease of use does not come at the expense of flexibility. Both full and split tunnel VPNs can be configured easily. New sites can similarly be added with a few simple clicks.
 Application-Aware Firewall
Application-Aware Firewall
![]() An integrated application-aware stateful firewall secures your network from malicious entities threatening today's networks. It's no longer enough to simply block protocols, hosts, and ports – a firewall must also be user, content, and application aware.
An integrated application-aware stateful firewall secures your network from malicious entities threatening today's networks. It's no longer enough to simply block protocols, hosts, and ports – a firewall must also be user, content, and application aware.
Protect your network using an integrated Snort-based intrusion detection system (IDS) featuring signature, protocol, and anomaly-based inspection. Use custom firewall rules to secure your network, allowing only approved, essential services and connections. Easily segregate voice, video, and data traffic, and deploy global firewall rules across VPN networks with a single click.
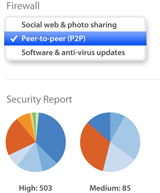
Intrusion Prevention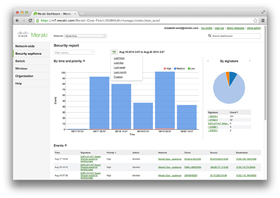
![]() Every Cisco Meraki MX Security Appliance supports unparalleled threat prevention via an integrated Sourcefire engine. Networks can be secured in seconds from the latest exploits, vulnerabilities, viruses, rootkits and more, with threat definitions automatically updated for bleeding edge protection.
Every Cisco Meraki MX Security Appliance supports unparalleled threat prevention via an integrated Sourcefire engine. Networks can be secured in seconds from the latest exploits, vulnerabilities, viruses, rootkits and more, with threat definitions automatically updated for bleeding edge protection.
View comprehensive security reports, displayed directly in the intuitive Meraki dashboard, from any Internet-accessible device. Data is presented in real time, allowing IT admins to quickly gauge current threat status—as well as view historical trends—for informed decision-making.
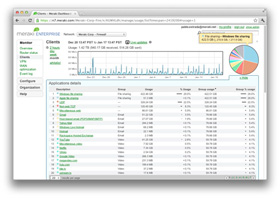 Control Applications, Users, and Devices
Control Applications, Users, and Devices
![]() The MX was purpose-built for modern, multi-use networks, providing extensive visibility and control over users, content, and applications. Far beyond simple host- and port-based solutions, the MX's Layer 7 fingerprinting classifies evasive and encrypted applications including P2P. Block unwanted web traffic with CIPA-compliant content filtering, throttle bandwidth hogs like Netflix and BitTorrent, and even prioritize productivity apps like VoIP.
The MX was purpose-built for modern, multi-use networks, providing extensive visibility and control over users, content, and applications. Far beyond simple host- and port-based solutions, the MX's Layer 7 fingerprinting classifies evasive and encrypted applications including P2P. Block unwanted web traffic with CIPA-compliant content filtering, throttle bandwidth hogs like Netflix and BitTorrent, and even prioritize productivity apps like VoIP.
The MX also provides insight into the users on the network, identifying clients by device type (e.g., iPads) and even username. Inspect, throttle, or block users, and integrate with Active Directory to apply different policies to different classes of users.
Content Filtering
![]()
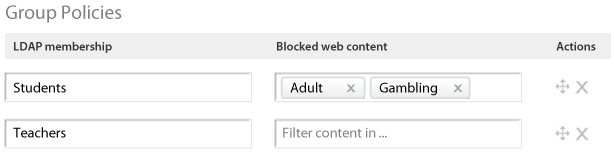 The MX's CIPA-compliant content filter enables administrators to block categories of content (adult, drugs, gambling, etc.) as well as individual URLs. Active Directory integration allows for different content filtering policies for different groups of users. The MX automatically refreshes its filtering lists from the cloud, so that your rules are always up to date, even as websites change.
The MX's CIPA-compliant content filter enables administrators to block categories of content (adult, drugs, gambling, etc.) as well as individual URLs. Active Directory integration allows for different content filtering policies for different groups of users. The MX automatically refreshes its filtering lists from the cloud, so that your rules are always up to date, even as websites change.
Built-in Google SafeSearch and YouTube for Schools enable a safe and secure learning environment without additional appliances or complex configuration. Integrated web caching dramatically accelerates browsing for users watching videos or using online apps.
WAN Optimization
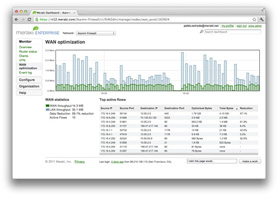
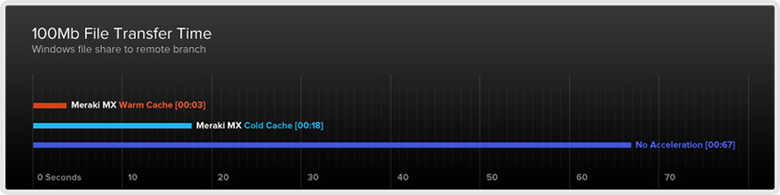
![]() Reduce intersite application bandwidth by up to 99% and accelerate CIFS, FTP, HTTP, and TCP traffic by up to 209x with the MX. A state-of-the-art WAN optimization engine uses advanced algorithms, deduplication, compression, and hard-disk based caching to make the WAN feel like a LAN.
Reduce intersite application bandwidth by up to 99% and accelerate CIFS, FTP, HTTP, and TCP traffic by up to 209x with the MX. A state-of-the-art WAN optimization engine uses advanced algorithms, deduplication, compression, and hard-disk based caching to make the WAN feel like a LAN.
Integrated web caching dramatically accelerates browsing for users watching videos or using online apps.
Built-in WAN optimization aids in server consolidation and private cloud initiatives, as well as any distributed network where end-user bandwidth costs or performance are a priority.
Smart Link Bonding
![]()
 Connect your branch with multiple WAN links, e.g., cable, DSL, T1, or even 3G/4G. Configure the MX to balance traffic between primary uplinks and failover to 3G/4G if those connections go down.
Connect your branch with multiple WAN links, e.g., cable, DSL, T1, or even 3G/4G. Configure the MX to balance traffic between primary uplinks and failover to 3G/4G if those connections go down.
The MX's Smart Link Bonding increases bandwidth and reduces cost. Supplement a T1 with an affordable DSL connection, increasing bandwidth for video and cloud applications. For maximum cost savings, forgo leased lines altogether by deploying the MX's site-to-site VPN over DSL, cable, or 3G/4G for secure, redundant, inexpensive connectivity.
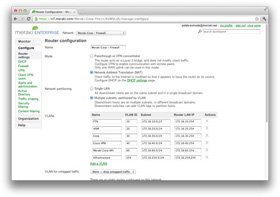 Branch Routing
Branch Routing
![]() The MX provides a complete networking solution, with a host of networking services for branch environments. Manage IP addresses with built-in DHCP and NAT. Enforce DMZs, punch firewall holes in seconds, segregate traffic with VLANs, and create routes through an intuitive web interface.
The MX provides a complete networking solution, with a host of networking services for branch environments. Manage IP addresses with built-in DHCP and NAT. Enforce DMZs, punch firewall holes in seconds, segregate traffic with VLANs, and create routes through an intuitive web interface.
Networking features integrate seamlessly with site to site VPN, stateful firewall, and other services, eliminating the need for an external branch router in most environments.
Bonjour Gateway
![]()
 The MX includes an integrated Bonjour gateway, enabling seamless support of Apple TVs, printers, AirPlay mirroring, and any other Bonjour server device. Selective bridging of services with subnet filtering allows for Bonjour support without overloading the network with multicast traffic.
The MX includes an integrated Bonjour gateway, enabling seamless support of Apple TVs, printers, AirPlay mirroring, and any other Bonjour server device. Selective bridging of services with subnet filtering allows for Bonjour support without overloading the network with multicast traffic.
The MX's intuitive configuration interface simplifies management of large-scale networks with many Apple devices, allowing for Bonjour support to be enabled with just a few clicks.
MX Cloud Managed Security Appliance Series Solutions:
Cisco Meraki MX Security Appliances make it easy to deploy high quality network infrastructure to large numbers of distributed sites. Since the MX is 100% cloud managed, installation and remote management is simple. The MX has a comprehensive suite of network services, elimi - nating the need for multiple appliances. Services include a next-generation firewall, content filtering, web search filtering, intrusion detection, web caching, WAN optimization, and link bonding with failover.
Eliminates 6 complex appliances with a single, easy to manage platform.

- Application-aware traffic control: set bandwidth policies based on Layer 7 application type (e.g., YouTube, Skype, P2P).
- Content filtering: CIPA-compliant content filter, web search filtering (Google/Bing) , and YouTube for Schools.
- Intrusion detection: PCI-compliant IDS sensor using industry-leading Snort database from Sourcefire.
- Anti-virus and anti-phishing: flow-based protection engine powered by Kaspersky.
- Identity-based filtering and application bandwidth management
Industry-leading Cloud Management
- Unified WAN, LAN, and wireless LAN management through a web- based dashboard.
- Template based settings scale easily from small deployments to large, multi-site deployments with tens of thousands of devices.
- Role-based administration, email alerts on configuration change, connectivity issues and power loss, auditable change logs.
- Summary reports with user, device, and application usage details archived in the cloud.
- Site-to-site VPN: automatic routing table generation, provisioning and key exchange via Cisco Meraki's secure cloud.
- Interoperates with standards-based IPsec VPNs.
- Automated MPLS to VPN failover
- Client VPN: L2TP IPsec support for native Windows, Mac OS X, iPad and Android clients with no per-user licensing fees
Branch Gateway Services
- Built-in DHCP, NAT, QoS, and VLAN management services.
- Web caching: accelerates frequently accessed content.
- Link bonding: combines multiple WAN links into a single high- speed interface, with policies for QoS, traffic shaping, and failover.
- Layer 3 failover: automatic detection of layer 2 and layer 3 outages and fast failover, including 3G/4G USB modems.
- WAN optimization: data redundancy elimination, protocol optimization, and compression provide bandwidth savings up to 99%.
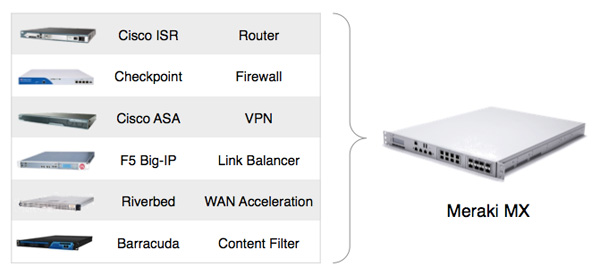
Consolidate up to six devices with a single Cisco Meraki MX appliance
Cloud Managed Architecture
Built on Cisco Meraki's award-winning cloud-managed architecture, the MX is the only 100% cloud-managed networking and security appliance. MX appliances self-provision, automatically pulling policies and configuration settings from the cloud. Powerful remote tools provide network-wide visibility and control, and enable administration without on-site networking expertise.
Cloud services deliver seamless firmware and security signature updates, automatically establish site-to-site VPN tunnels, and provide 24x7 network monitoring. Moreover, the MX's browser- based management dashboard completely eliminates the need for training.
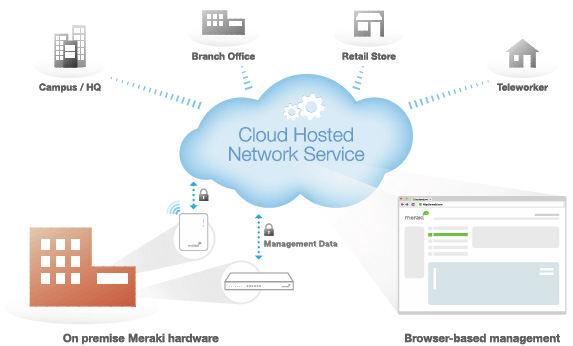
Cisco Meraki Cloud Management Architecture
Ironclad Security for Edge Networks
The MX hardware platform is purpose-built for Layer 7 deep packet inspection, with advanced security features including IPS, content filtering, web search filtering, anti-virus / anti-phishing, and IPsec VPN connectivity, while providing the throughput and capacity for modern, bandwidth-intensive networks.
Layer 7 fingerprinting technology lets administrators identify unwanted content and applications and prevent recreational apps like BitTorrent from wasting precious bandwidth.
The integrated Sourcefire SNORTengine delivers superior intrusion prevention coverage, a key requirement for PCI 2.0 compliance. The MX also uses the Webroot BrightCloud URL categorization database for CIPA / IWF compliant content-filtering, and Kaspersky SafeStream engine for anti-virus / anti-phishing filtering.
Best of all, these industry-leading Layer 7 security engines and signatures are always kept up-to-date via the cloud, simplifying network security management and providing peace-of-mind to IT administrators.
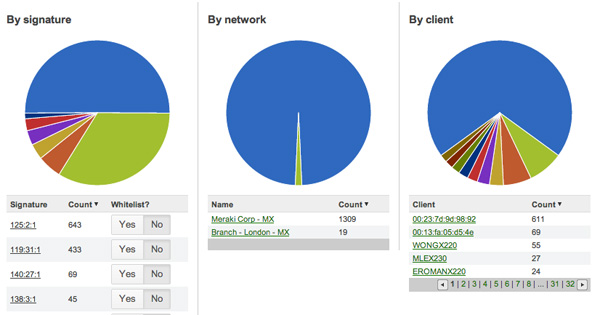
Organization Level Threat Assessment
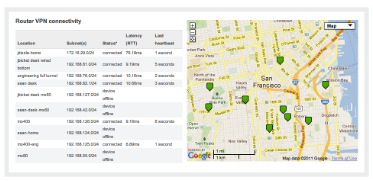
Auto Configuring Site-to-Site VPN
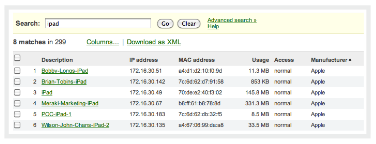
User and Device Fingerprints
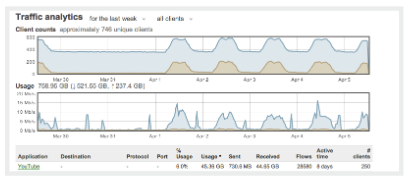
Next Gen Application Firewall and Traffic Visibility
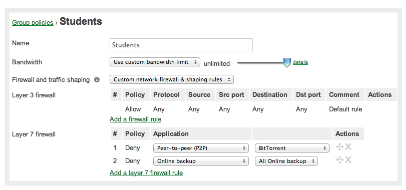
Identity Based Policy Management
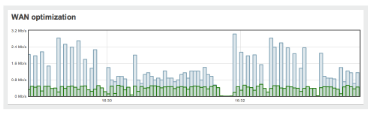
WAN Optimization
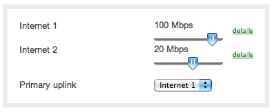
Link Bonding and Failover
Powerful Hardware Platform
The MX hardware platform is purpose-built for cloud management, with CPU and memory resources designed to provide application and content-aware security at the edge. The MX's robust platform enables advanced features like layer 7 application traffic shaping, content filtering, antivirus/antiphishing, and site-to-site VPN, while providing the throughput and capacity for modern, high-density networks.
Inside the Cisco Meraki MX
MX400 shown, features vary by model
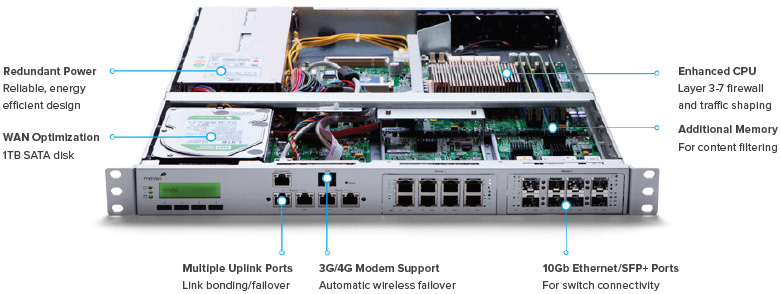
Increased Reliability with Multiple WAN Links and 3G/4G Failover
Multiple WAN ports with balancing and failover enable the use of redundant commodity Internet connections, providing additional bandwidth and higher reliability. For remote sites where multiple wireline providers are difficult to secure, the Cisco Meraki MX can fail over to 3G/4G wireless Internet connections
Reduce Bandwidth Costs with Web Caching and WAN Optimization
Web caching temporarily stores video, media, and web documents, lowering bandwidth usage and accelerating the download speed of Inter - net content like YouTube videos and other media.
WAN optimization dramatically improves application performance and reduce bandwidth requirements at remote sites. All Cisco Meraki MX appliances include WAN optimization at no additional charge. The MX60 and MX60W feature basic WAN optimization, while the MX80, MX100, MX400, and MX600 feature advanced WAN optimization.
Basic WAN optimization includes link compression and protocol optimization. Link compression reduces TCP traffic by 20% - 30%, and proto - col optimization accelerates Windows File Sharing (CIFS), FTP, and HTTP transfers.
Advanced WAN optimization adds high-capacity byte-level caching for additional performance improvements, employing a universal data store to maximize the effectiveness of the cache.
MX64W with 802.11ac Wireless
The MX64W integrates Cisco Meraki's award-winning wireless technology with the powerful MX network security features in a compact form factor ideal for branch offices or small enterprises:
- Dual-band 802.11n/ac, 2x2 MIMO with 2 spatial streams
- Unified management of network security and wireless
- Integrated enterprise security and guest access

MX64W Security Appliance
Z1 Telecommuter Gateway
The Z1 Telecommuter Gateway extends the power of the Cisco Meraki dashboard and cloud-based centralized management to employees, IT staff and executives working from home.
Using the patent-pending Cisco Meraki Auto VPN, Administrators can extend network services including VoIP and remote desktop (RDP) to remote employees with a single-click, provide wired and wireless access, and increase end-user pro - ductivity through Layer 7 traffic shaping and prioritization.
- 1 x 802.11b/g/n radio, 1 x 802.11a/n radio, 2x2 MIMO with 2 spatial streams
- Site-to-site (IPsec) VPN using Cisco Meraki Auto VPN
- Layer 7 application visibility and traffic shaping

Z1 Telecommuter Gateway
Lifetime Warranty with Next-day Advanced Replacement
Cisco Meraki MX appliances include a limited lifetime hardware warranty that provides next-day advance hardware replacement. Cisco Meraki's simplified software and support licensing model also combines all software upgrades, centralized systems management, and phone support under a single, easy-to-understand model.
Cloud Management:
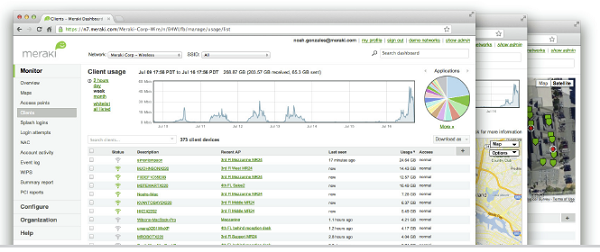
Cisco Meraki's cloud based management provides centralized visibility & control over Cisco Meraki's wired & wireless networking hardware, without the cost and complexity of wireless controllers or overlay management systems. Integrated with Cisco Meraki's entire product portfolio, cloud management provides feature rich, scalable, and intuitive centralized management for networks of any size.
Highlights
- Unified visibility and control of the entire network via a single dashboard: wireless, switching, and security appliances
- Streamlines large networks with tens of thousands of endpoints
- Zero-touch provisioning for rapid deployment
- Built-in multi site network management tools
- Automated network monitoring and alerts
- Intuitive interface eliminates costly training or added staff
- Network tagging engine - search and sync settings by tag
- Role-based administration and auditable change logs
- Continuous feature updates delivered from the cloud
- Highly available and secure (PCI / HIPAA compliant)
Cloud Managed Networks
Cisco Meraki's hardware products are built from the ground up for cloud management. As a result, they come out of the box with centralized control, layer 7 device and application visibility, real time web-based diagnostics, monitoring, reporting, and much more.
Cisco Meraki networks deploy quickly and easily, without training or dedicated staff. Moreover, Cisco Meraki provides a rich feature set that provides complete control over devices, users, and applications, allowing for flexible access policies and rich security without added cost or complexity.
Cisco Meraki's cloud management provides the features, security, and scalability for networks of any size. Cisco Meraki scales from small sites to campuses, and even distributed networks with thousands of sites. Cisco Meraki devices, which self-provision via the cloud, can be deployed in branches without IT. Firmware and security signature updates are delivered seamlessly, over the web. With the cloud, branches can automatically establish secure VPN tunnels between one another with a single click.
With a secure, PCI and HIPAA compliant architecture and fault tolerant design that preserves local network functionality during WAN outages, Cisco Meraki is field proven in high security and mission critical network applications.
Cloud Management Architecture
Cisco Meraki's architecture provides feature rich network management without on-site management appliances or WiFi controllers.
Every Cisco Meraki device - including wirelesss access points, Ethernet switches, and security appliances - connects over the Internet to Cisco Meraki's datacenters, which run Cisco Meraki's cloud management platform. These connections, secured via SSL, utilize a patented protocol that provides real time visibility and control, yet uses minimal bandwidth overhead (typically 1 kbps or less.)
In place of traditional command-line based network configuration, Cisco Meraki provides a rich web based dashboard, providing visibility and control over up to tens of thousands of Cisco Meraki devices, anywhere in the world. Tools, designed to scale to large and distributed networks, make policy changes, firmware updates, deploying new branches, etc. simple and expedient, regardless of size or location. Cisco Meraki's real time protocols combine the immediacy of on-premise management applications with the simplicity and centralized control of a cloud application.
Every Cisco Meraki device is engineered for cloud management. Specifically, this means that Cisco Meraki devices are designed with memory and CPU resources to perform packet processing, QoS, layer 3-7 security, encryption, etc. at the network edge. As a result, no network traffic passes through the cloud, with the cloud providing management functionality out of the data path. This architecture enables networks to scale horizontally, adding capacity simply by adding more endpoints, without concern for centralized bottlenecks or chokepoints. Equally important, since all packet processing is performed on premise, end-user functionality is not compromised if the network's connection to the cloud is interrupted.
Cisco Meraki's cloud platform is designed to spread computation and storage across independent server clusters in geographically isolated datacenters. Any server or datacenter can fail without affecting customers or the rest of the system. Additionally, Cisco Meraki's datacenter design is field proven to support tens of thousands of endpoints.
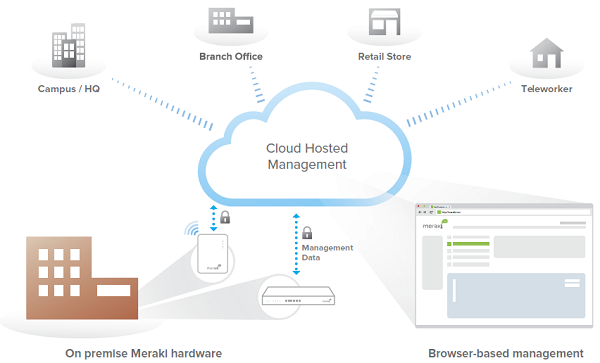
Cloud Management Architecture
Powerful Insight and Troubleshooting Tools
Cisco Meraki's cloud architecture delivers powerful insight and includes live tools integrated directly into the dashboard, giving instant analysis of performance, connectivity, and more. Using live tools, network administrators no longer need to go on site to perform routine troubleshooting tests. Visibility into devices, users, and applications gives administrators the information needed to enforce security policies and enable the performance needed in today's demanding network environments.
Troubleshooting tools such as ping, traceroute, throughput, and even live packet captures are integrated directly into the Cisco Meraki dashboard, dramatically reducing resolution times and enabling troubleshooting at remote locations without on-site IT staff.
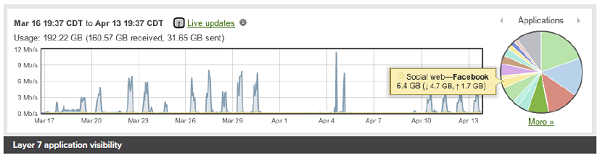
Layer 7 application visibility
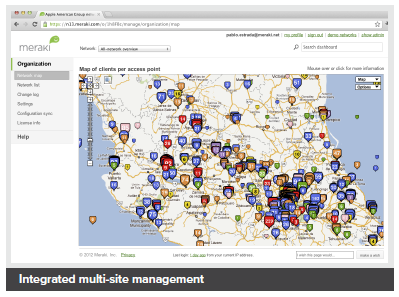
Integrated multi-site management
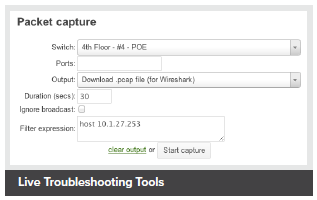
Live Troubleshooting Tools
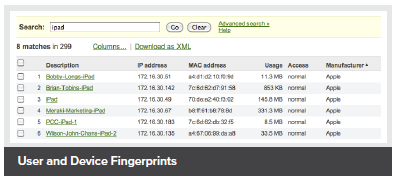
User and Device Fingerprints
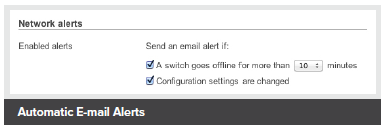
Automatic E-mail Alerts
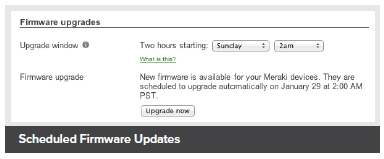
Scheduled Firmware Updates
Out-of-Band Control Plane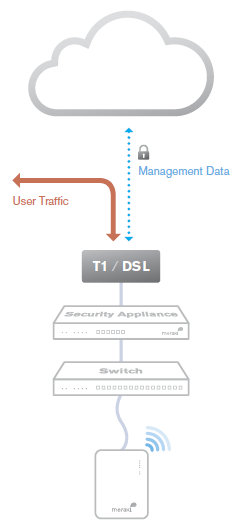
Cisco Meraki's out-of-band control plane separates network management data from user data. Management data (e.g., configuration, statistics, monitoring, etc.) flows from Cisco Meraki devices (wireless access points, switches, and security appliances) to Cisco Meraki's cloud over a secure Internet connection. User data (web browsing, internal applications, etc.) does not flow through the cloud, instead flowing directly to its destination on the LAN or across the WAN.
Advantages of an out of band control plane:
Scalability
- Unlimited throughput: no centralized controller bottlenecks
- Add devices or sites without MPLS tunnels
- Add switching capacity without stacking limitations
Reliability
- Redundant cloud service provides high availability
- Network functions even if management traffic is interrupted
Security
- No user traffic passes through Cisco Meraki's datacenters
- Fully HIPAA / PCI compliant
What happens if a network loses connectivity to the Cisco Meraki cloud?
Because of Cisco Meraki's out of band architecture, most end users are not affected if Cisco Meraki wireless APs, switches, or security appliances cannot communicate with Cisco Meraki's cloud services (e.g., because of a temporary WAN failure):
- Users can access the local network (printers, file shares, etc.)
- If WAN connectivity is available, users can access the Internet
- Network policies (firewall rules, QoS, etc.) continue to be enforced
- Users can authenticate via 802.1X/RADIUS and can roam wirelessly between access points
- Users can initiate and renew DHCP leases
- Established VPN tunnels continue to operate
- Local configuration tools are available (e.g., device IP configuration)
While Cisco Meraki's cloud is unreachable, management, monitoring, and hosted services are temporarily unavailable:
- Configuration and diagnostic tools are unavailable
- Usage statistics are stored locally until the connection to the cloud is re-established, at which time they are pushed to the cloud
- Splash pages and related functionality are unavailable
Cisco Meraki Datacenter Design
Cisco Meraki's cloud management service is colocated in tier-1, SAS70 type II certified datacenters. These datacenters feature state of the art physical and cyber security and highly reliable designs. All Cisco Meraki services are replicated across multiple independent datacenters, so that customer-facing services fail over rapidly in the event of a catastrophic datacenter failure.
- Five geographically dispersed datacenters
- Every customer's data (network configuration and usage metrics) replicated across three independent datacenters
- Real-time data replication between datacenters (within 60 seconds)
- Nightly archival backups
Availability Monitoring
- 24x7 automated failure detection — all servers are tested every five minutes from multiple locations
- Rapid escalation procedures across multiple operations teams
- Independent outage alert system with 3x redundancy
Disaster Recovery
- Rapid failover to hot spare in event of hardware failure or natural disaster
- Out of band architecture preserves end-user network functionality, even if connectivity to Cisco Meraki's cloud services is interrupted
- Failover procedures drilled weekly
Cloud Services Security
- 24x7 automated intrusion detection
- Protected via IP and port-based firewalls
- Access restricted by IP address and verified by public key (RSA)
- Systems are not accessible via password access
- Administrators automatically alerted on configuration changes
Physical Security
- High security card keys and biometric readers control facility access
- All entries, exits, and cabinets are monitored by video surveillance
- Security guards monitor all traffic into and out of the datacenters 24x7, ensuring that entry processes are followed
- Only configuration and usage statistics are stored in the cloud
- End user data does not traverse through the datacenter
- All sensitive data (e.g., passwords) stored in encrypted format
Disaster Preparedness
- Datacenters feature sophisticated sprinkler systems with interlocks to prevent accidental water discharge
- Diesel generators provide backup power in the event of power loss
- UPS systems condition power and ensure orderly shutdown in the event of a full power outage
- Each datacenter has service from at least two top-tier carriers
- Seismic bracing for raised floor, cabinets, and support systems
- In the event of a catastrophic datacenter failure, services fail over to another geographically separate datacenter
Environmental Controls
- Over-provisioned HVAC systems provide cooling and humidity control
- Flooring systems are dedicated for air distribution
Certification
- Cisco Meraki datacenters are SAS70 type II certified
- PCI level 1 certified
Service Level Agreement
- Cisco Meraki's cloud management is backed by a 99.99% uptime SLA. See https://meraki.cisco.com/trust for details.
Security Tools for Administrators
In addition to Cisco Meraki's secure out-of-band architecture and hardened datacenters, Cisco Meraki provides a number of tools for administrators to maximize the security of their network deployments. These tools provide optimal protection, visibility, and control over your Cisco Meraki network.
Two-factor authentication
Two-factor authentication adds an extra layer of security to an organization's network by requiring access to an administrator's phone, in addition to her username and password, in order to log in to Cisco Meraki's cloud services. Cisco Meraki's two factor authentication implementation uses secure, convenient, and cost effective SMS technology: after entering their username and password, an administrator is sent an a one-time passcode via SMS, which they must enter before authentication is complete. In the event that a hacker guesses or learns an administrator's password, she still will not be able to access the organization's account, as the hacker does not have the administrator's phone. Cisco Meraki includes two-factor authentication for all enterprise users at no additional cost.Password policies
Organization-wide security policies for Cisco Meraki accounts help protect access to the Cisco Meraki dashboard. These tools allow administrators to:
- Force periodic password changes (e.g., every 90 days)
- Require minimum password length and complexity
- Lock users out after repeated failed login attempts
- Disallow password reuse
- Restrict logins by IP address
Role-based administration
Role-based administration lets supervisors appoint administrators for specific subsets of an organization, and specify whether they have read-only access to reports and troubleshooting tools, administer managed guest access, or can make configuration changes to the network. This minimizes the chance of accidental or malicious misconfiguration, and restricts errors to isolated parts of the network.Configuration change alerts
The Cisco Meraki system can automatically send human-readable email and text message alerts when configuration changes are made, enabling the entire IT organization to stay abreast of new policies. Change alerts are particularly important with large or distributed IT organizations.Configuration and login audits
Cisco Meraki logs the time, IP, and approximate location (city, state) of logged in administrators. A searchable configuration change log indicates what configuration changes were made, who they were made by, and which part of the organization the change occurred in.SSL certificates
Cisco Meraki accounts can only be accessed via https, ensuring that all communication between an administrator's browser and Cisco Meraki's cloud services is encrypted.Idle Timeout
30 seconds before being logged out, users are shown a notice that allows them to extend their session. Once time expires, users are asked to log in again.
Compare:
Lifetime Warranty with Next-day Advanced Replacement
Cisco Meraki MX appliances include a limited lifetime hardware warranty that provides next-day advance hardware replacement. Cisco Meraki’s simplified software and support licensing model also combines all software upgrades, centralized systems management, and phone support under a single, easy-to-understand model. For complete details, please visit meraki.cisco.com/support.
Product Options
| MX64(W) | MX65(W) | MX84 | MX100 | MX400 | MX600 | |
| Recommended Use Cases | Small retail branch, small clinic | Small retail branch, small clinic | Medium sized branch | Large branch | K-12 firewall / VPN concentrator | Large K-12 firewall, VPN concentrator |
| Recommended Max Clients | 50 | 50 | 200 | 500 | 2,000 | 10,000 |
| Stateful Firewall Throughput | 250 Mbps | 250 Mbps | 500 Mbps | 750 Mbps | 1 Gbps | 1 Gbps |
| Advanced Security Throughput | 100 Mbps | 100 Mbps | 200 Mbps | 600 Mbps | 1 Gbps | 1 Gbps |
| Maximum VPN sessions | 25 | 25 | 100 | 250 | 1,000 | 5,000 |
| Interfaces | 5 x GbE | 12 x GbE (2 PoE+) | 10 x GbE 2 x GbE (SFP) | 9 x GbE 2 x GbE (SFP) | 4 x GbE | 4 x GbE |
| Additional Interface Modules | N/A | N/A | N/A | N/A | 8 x GbE (RJ45) 8 x GbE (SFP) 2 x 10GbE (SFP+) (2 modules max) |
8 x GbE (RJ45) 8 x GbE (SFP) 2 x 10GbE (SFP+) (2 modules max) |
| Web Caching | N/A | N/A | Yes | Yes | Yes | Yes |
| Hard Drive* | N/A | N/A | 1 TB | 1 TB | 1 TB | 4 x 1 TB (RAID) |
| USB for 3G/4G Failover | Yes | Yes | Yes | Yes | Yes | Yes |
| Mounting | Desk / Wall | Desk / Wall | 1U rack | 1U rack | 1U rack | 2U rack |
| Dimensions | 9.5” x 5.2” x 1” (239mm x 132mm x 25mm) | 10.0” x 5.2” x 1” (256mm x 132mm x 25mm) | 19.0” x 10.0 “ x 1.75” (483 mm x 254 mm x 44 mm) | 19.0” x 10.0 “ x 1.75” (483 mm x 254 mm x 44 mm) | 19.0” x 22.0 “ x 1.75” (483 mm x 559 mm x 44 mm) | 19.0” x 22.0 “ x 3.5” (483 mm x 559 mm x 89 mm) |
| Weight | 3.04 lb (1.4 kg) | 3.37 lb (1.53 kg) | 9 lb (4.1kg) | 9 lb (4.1kg) | 33 lb (15.0 kg) | 53 lb (24.0 kg) |
| Power Supply | 18W DC (included) | 90W DC (included) | 100-220V 50/60Hz AC | 100-220V 50/60Hz AC | 100-220V 50/60Hz AC (dual) | 100-220V 50/60Hz AC (dual) |
| Power Load (idle/max) | 4W / 10W (MX64) 6W / 13W (MX64W) |
6W / 72W (MX65) 9W / 79W (MX65W) |
26W / 32W | 30W / 55W | 123W / 215W | 132W / 226W |
| Operating Temperature | 32°F to 104°F (0°C to 40°C) | 32°F to 104°F (0°C to 40°C) | 32°F to 104°F (0°C to 40°C) | 32°F to 104°F (0°C to 40°C) | 32°F to 104°F (0°C to 40°C) | 32°F to 104°F (0°C to 40°C) |
| Humidity | 5% to 95% | 5% to 95% | 5% to 95% | 5% to 95% | 5% to 95% | 5% to 95% |
*Note: Hard drive is used for web caching.
Specifications:
Management
- Managed via the web using the Cisco Meraki dashboard
- Single pane-of-glass into managing wired and wireless networks
- Zero-touch remote deployment (no staging needed)
- Automatic firmware upgrades and security patches
- Templates based multi-network management
- Org-level two-factor authentication and single sign-on
- Role based administration with change logging and alerts
Monitoring and Reporting
- Throughput, connectivity monitoring and email alerts
- Detailed historical per-port and per-client usage statistics
- Application usage statistics
- Org-level change logs for compliance and change management
- VPN tunnel and latency monitoring
- Network asset discovery and user identification
- Periodic emails with key utilization metrics
- Syslog integration
Remote Diagnostics
- Live remote packet capture
- Real-time diagnostic and troubleshooting tools
- Aggregated event logs with instant search
Network and Security Services
- Stateful firewall, 1:1 NAT, DMZ
- Identity-based policies
- Auto VPN: Automated site-to-site (IPsec) VPN, for hub-and-spoke or mesh topologies
- Client (IPsec L2TP) VPN
- Multiple WAN IP, PPPoE, NAT
- VLAN support and DHCP services
- Static routing
- User and device quarantine
WAN Performance Management
- Web caching
- WAN link aggregation
- Automatic Layer 3 failover (including VPN connections)
- 3G / 4G USB modem failover
- Application level (Layer 7) traffic analysis and shaping
- Ability to choose WAN uplink based on traffic type
- Note: Web caching is not available on the MX64 or MX64W models.
Advanced Security Services
- Content filtering (Webroot BrightCloud CIPA compliant URL database)
- Web search filtering (including Google / Bing SafeSearch)
- YouTube for Schools
- Intrusion-prevention sensor (Sourcefire SNORT® based)
- Anti-virus engine and anti-phishing filtering (Kaspersky SafeStream II engine)
- Geography based firewall rules (MaxMind Geo-IP database)
- Note: Advanced security services require Advanced Security license.
Regulatory
- FCC (US)
- CB (IEC)
- CISPR (Australia/New Zealand)
Warranty
- Full lifetime hardware warranty with next-day advanced replacement included.
Accessories:
The Cisco Meraki MX100, MX400, and MX600 models support pluggable optics for high-speed backbone or link aggregation connections between wiring closets or to aggregation switches. Cisco Meraki offers several standards-based Gigabit and 10 Gigabit pluggable modules. Each appliance has also been tested for compatibility with several third-party modules.

8 x 1 GbE Copper Interface Module

8 x 1 GbE SFP Interface Module

2 x 10 GbE SFP+ Interface Module

1 GbE SFP Copper Module
- For: MX100, MX400, MX600
- Standard: 1000BASE-T
- Range: 100m

1 GbE SFP SX Fiber Transceiver
- For: MX100, MX400, MX600
- Standard: 1000BASE-SX
- Range: 550m

10 GbE SFP+ Short Range Fiber Transceiver
- For: MX400, MX600
- Standard: 10GBASE-SR
- Range: 400m

Twinax Cable with SFP+ Connectors
- For: MX400, MX600
- Standard: SFP+ Direct Attach (10GSFP+Cu)
- Range: 1m
| Model | Description |
|---|---|
| IM-8-CU-1GB | Cisco Meraki 8 x 1 GbE Copper Interface Module for MX400 and MX600 |
| IM-8-SFP-1GB | Cisco Meraki 8 x 1 GbE SFP Interface Module for MX400 and MX600 |
| IM-2-SFP-10GB | Cisco Meraki 2 x 10 GbE SFP+ Interface Module for MX400 and MX600 |
| MA-SFP-1GB-SX | Cisco Meraki 1 GbE SFP SX Fiber Module (1000BASE-SX, range: 550m) |
| MA-SFP-10GB-SR | Cisco Meraki 10 GbE Short Range SFP+ Module (10GBASE-SR, range: 400m) |
| MA-CBL-TA-1M | Cisco Meraki 10 GbE Twinax Cable with SFP+ Connectors (10GSFP+Cu, range: 1m) |
Note: Please refer to Cisco Meraki.com for additional single-mode and multi-mode fiber transceiver modules
License Editions:
An organization must have a valid Enterprise Edition license or Advanced Security Edition license for the MX series in order to work properly. Each organization is licensed for a maximum number of security appliances for a certain amount of time (typically from one year to five years). For example, the organization may be licensed for 25 appliances with the Enterprise Edition through January 30, 2012.
In addition, each organization is required to use either the Enterprise Edition or the Advanced Security Edition uniformly. For example, you can have all 25 appliances using Enterprise Edition or Advanced Security Edition, but you cannot have 20 appliances using one edition and 5 using the other edition. If you wish to use Enterprise Edition for some appliances and Advanced Security Edition for other appliances, you need to create two organizations, one for your appliances with the Enterprise Edition, and another for the appliances with the Advanced Security Edition.
You can manage a given organization's licenses on the Organization > License info page. The page displays the following information:
- Status: OK or problem
- Expiration date
- MX Advanced Security Enabled or Disabled
- Licensed device limit for each device type
- Current device count for each device type
- License history (list of licenses that have been applied to the network)
Enterprise vs. Advance Security license
| The following table provides a list of the major features and the required licensing. | ||
|---|---|---|
| Feature | Enterprise license | Advanced Security license |
| Stateful firewall | ||
| VLAN to VLAN routing | ||
| Link bonding / failover | ||
| 3G / 4G failover | ||
| Traffic shaping / prioritization | ||
| WAN optimization | ||
| Site-to-site VPN | ||
| Client VPN | ||
| MPLS to VPN Failover | ||
| Splash pages | ||
| Configuration templates | ||
| HTTP content caching | ||
| Group Policies | ||
| Client connectivity alerts | ||
| Intrusion detection / prevention | ||
| Content filtering | ||
| Anti-virus and anti-phishing | ||
| Youtube for Schools | ||
| Web Search Filtering | ||
Adding licenses
You can add a license by clicking Add another license. You will then have two actions, or "operations", to choose from:
- License more devices: increases the number of devices that can exist within this Cisco Meraki Dashboard organization.
- Renew my Dashboard license: extends the licensing period of this Cisco Meraki Dashboard organization. You must renew the license for all devices in the organization. You cannot renew licensing for only certain devices within the organization.
You cannot add an Enterprise MX license to an Advanced Security organization. Adding an Advanced Security license to an Enterprise organization will convert that organization to Advanced Security. All existing Enterprise MX licenses will have their duration halved to compensate for the difference in the licensing costs, and the organization's license cotermination date will be adjusted accordingly.
Expired licenses or exceeding the licensed device limit
If an organization's license is expired or the number of devices in the organization exceeds the licensed limit, the administrator has 30 days to return the organization to a valid licensed state. During this grace period, the system reminds the administrator to add additional licenses. After 30 days, administrators are not able to access the Dashboard (except to add additional licenses) and all Cisco Meraki equipment in the organization will cease to function.
Use Cases:
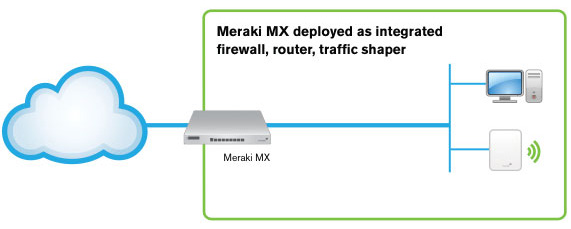
Cloud-Managed Multi-Service Router
Build an easy to deploy and reliable network that doesn't require costly solutions like MPLS tunnels. Deploy the MX series in missioncritical networks using link failover. Simplify access and visibility through cloud-managed site-to-site VPN. Secure remote networks using advanced security features like anti-virus filtering. Optimize network costs using traffic shaping.
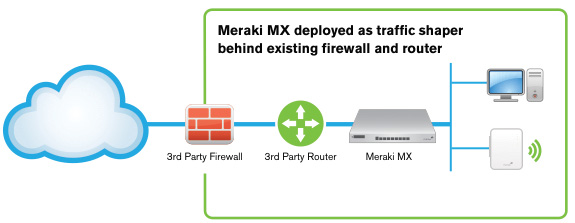
Inline Traffic Shaper and Network Monitor
The MX series are equally indispensable when deployed behind an existing firewall and router. Optimize network traffic with application-aware (layer 7) traffic shaping and firewall. Prioritize mission critical applications or VoIP traffic while setting limits on recreational traffic, e.g. peer-to-peer applications. Discover all client devices, identify users and monitor printers.
Documentation:
Download the Cisco Meraki MX Series Datasheet (PDF).
הערות תמחור:
- שימו לב: כל המחירים באתר כוללים מע"מ.
- החיוב יבוצע על פי שער "העברות והמחאות מכירה" של המטבע (דולר אמריקאי) ביום אישור ההזמנה.
- מחירי המוצרים וזמינותם כפופים לשינויים ללא הודעה מוקדמת.
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
המחיר שלנו: הצעת מחיר
Standard: SFP+ Direct Attach (10GSFP+Cu) Range: 1m
המחיר שלנו: הצעת מחיר
Standard: SFP+ Direct Attach (10GSFP+Cu) Range: 3m
המחיר שלנו: הצעת מחיר
